What this programs does:
Internet Security 2010 is a rogue anti-spyware program that is installed through the use of malware. Once installed, Internet 

Internet Security 2010
For more screen shots of this infection click on the image above.
There are a total of 8 images you can view.
Internet Security 2010 is typically bundled with numerous Trojans that display fake security alerts on your computer. For example, one Trojan will display a message when you login into Windows before you see your desktop. This message will state:
Security Warning!
Worm.Win32.NetSky detected on your machine.
It will then recommend that you purchase the program to remove the infection. When you start certain programs, another Trojan will display a message and then terminate the program. The message it will display is:
Application cannot be executed. The file is infected. Please activate your antivirus
software .
Some of the programs that will cause this message to be shown include Notepad, the CMD prompt, Freecell, Minesweeper, Nero, Windows Messenger, Microsoft Word, Microsoft Excel, Window calculator, Skype, and PowerPoint. This same Trojan will also display a warning when you try to run programs, such as Windows Media 
Windows can`t play the folowing media formats: AVI;WMV;AVS;FLV;MKV;MOV;3GP;MP4;MPG;MPEG;MP3;AAC;WAV;WMA;CDA;FLAC;M4A;MID. Update your video and sound codec to resolve this issue.
It will then prompt you to purchase VSCodec Pro, which is another rogue program, to fix the supposed problem. Just like the scan results, these security warnings are fake and are only being shown to try and convince you that your computer has a security problem.
As you can see, Internet Security 2010 was created to scare you into purchasing the program. Without a doubt, you should definitely not do so, and if you have, you should contact your credit card company and dispute the charges stating that the program is a scam. Finally, to remove Internet Security 2010 and any related malware please use the removal guide to remove it for free.
Threat Classification:
Advanced information:
View Internet Security 2010 files.
View Internet Security 2010 Registry Information.
Tools Needed for this fix:
Symptoms that may be in a HijackThis Log:
F2 - REG:system.ini: UserInit=C:\WINDOWS\system32\winlogon86.exe
O4 - HKLM\..\Run: [winupdate86.exe] C:\WINDOWS\system32\winupdate86.exe
O4 - HKCU\..\Run: [Internet Security 2010] C:\Program Files\InternetSecurity2010\IS2010.exe
O10 - Unknown file in Winsock LSP: c:\windows\system32\winhelper86.dll
O10 - Unknown file in Winsock LSP: c:\windows\system32\winhelper86.dll
Automated Removal Instructions for Internet Security 2010 using Malwarebytes' Anti-Malware: Your computer should now be free of the Internet Security 2010 program. If your current anti-virus solution let this infection through, you may want to consider purchasing the PRO version of Malwarebytes' Anti-Malware to protect against these types of threats in the future. If you are still having problems with your computer after completing these instructions, then please follow the steps outlined in the topic linked below: Preparation Guide For Use Before Using Malware Removal Tools and Requesting Help Associated Internet Security 2010 Files: Associated Internet Security 2010 Windows Registry Information:
rkill.com Download Link
Do not reboot your computer after running rkill as the malware programs will start again.
Malwarebytes' Anti-Malware Download Link
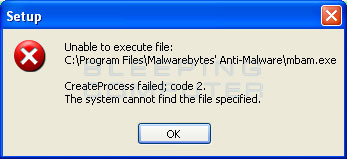
If you receive a code 2 error while installing Malwarebytes's, please press the OK button to close these errors as we will resolve them in future steps. The code 2 error will look similar to the image below.
Malwarebytes' EXE Download
When your browser prompts you where to save it to, please save it to the C:\program files\Malwarebytes' Anti-Malware\ folder. When downloading the file, it will have a random filename. Please leave the filename the way it is as it is important that it is not changed. You may want to write down the name of the file as you will need to know the name in the next step.
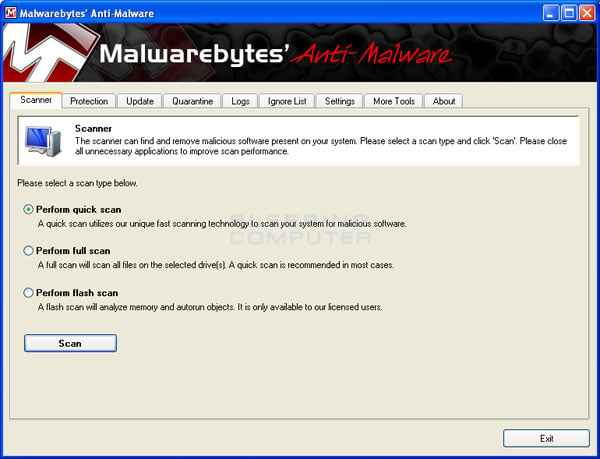
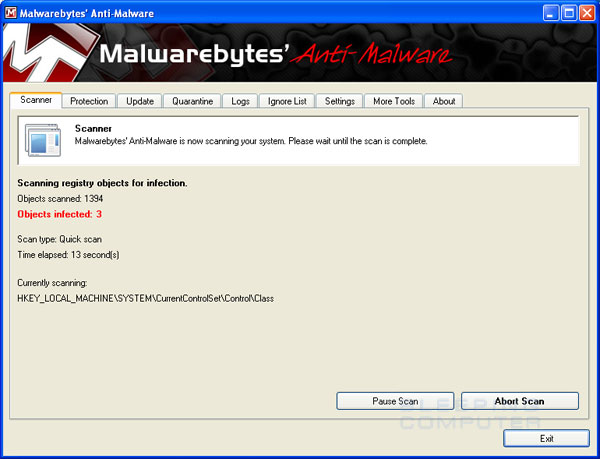
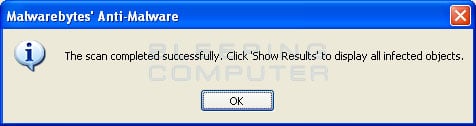
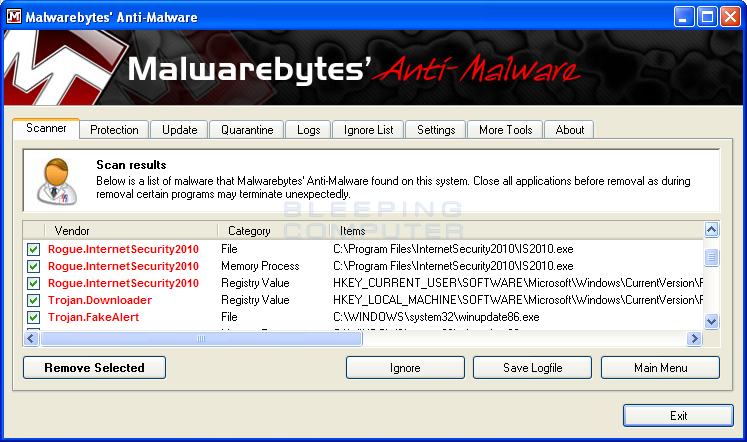
You should now click on the Remove Selected button to remove all the listed malware. MBAM will now delete all of the files and registry keys and add them to the programs quarantine. When removing the files, MBAM may require a reboot in order to remove some of them. If it displays a message stating that it needs to reboot, please allow it to do so. Once your computer has rebooted, and you are logged in, please continue with the rest of the steps.
c:\s
c:\Program Files\InternetSecurity2010
c:\Program Files\InternetSecurity2010\IS2010.exe
c:\WINDOWS\system32\41.exe
c:\WINDOWS\system32\winhelper86.dll
c:\WINDOWS\system32\winlogon86.exe
c:\WINDOWS\system32\winupdate86.exe
%UserProfile%\Application Data\Microsoft\Internet Explorer\Quick Launch\Internet Security 2010.lnk
%UserProfile%\Desktop\Internet Security 2010.lnk
%UserProfile%\Start Menu\Internet Security 2010.lnk HKEY_CURRENT_USER\Software\IS2010
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Internet Security 2010"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "winupdate86.exe"



















 Ansav is a free antivirus utility designed to identify, thwart and eliminate computer viruses and other malicious software (malware).
Ansav is a free antivirus utility designed to identify, thwart and eliminate computer viruses and other malicious software (malware).